Continuous validation, no-code provisioning, native OPA support for Terraform Cloud, and other new features are key upgrades to HashiCorp Terraform introduced at HashiConf Global 2022.
Today at HashiConf Global, we introduced a number of significant enhancements for HashiCorp Terraform that help users consistently provision and manage any cloud, infrastructure, and service. The announcements highlighted in the HashiConf keynote include capabilities for both Day 1 provisioning, Day 2 management, and beyond. Announcements included:
- Continuous validation for Terraform Cloud Business (beta)
- No-code provisioning for Terraform Cloud Business (beta)
- Native Open Policy Agent (OPA) support for Terraform Cloud (beta)
- General availability of Terraform 1.3
We’re also announcing several new features that weren’t covered in detail in the keynote, including Azure Provider Automation, beta support for Terraform Plugin Framework, and an integration with ServiceNow Service Graph.
Terraform Is Addressing New Challenges in the Cloud
Migration to the cloud has led organizations to adopt infrastructure automation to provision and manage their cloud resources. As organizations scale, they face challenges around maintaining code health and visibility, coping with inefficient manual workflows, and mitigating security or compliance issues.
Provisioning and managing infrastructure in a multi-cloud environment brings a whole new set of challenges, including managing disparate workflows and infrastructure sprawl, handling teams separated into silos, and dealing with gaps in critical skills. The Terraform enhancements introduced this week help address many of these issues users and organizations face as they standardize their infrastructure automation for multi-cloud.
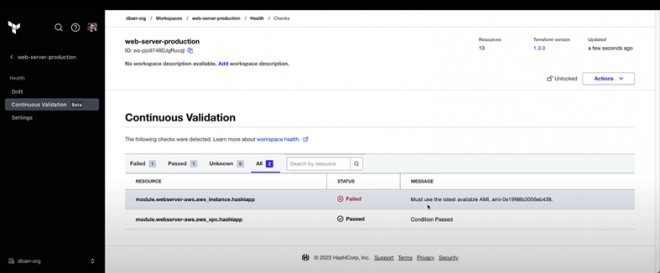
From Drift Detection to Continuous Validation
Once infrastructure is provisioned, it can be difficult to ensure the actual state of resources always reflects the recorded, desired state and health. What worked at the time of provisioning (service configuration, identity and access management, and anything utilized by an application’s business logic) may not continue to work properly post-deployment, even if the end result of a Terraform apply was successful.
At HashiConf Europe, we announced the availability of drift detection, which continuously checks infrastructure state to detect changes and provide alerts. Continuous validation represents the next step in Day 2 infrastructure management, expanding checks on your infrastructure beyond just configuration drift. Continuous validation provides long-term visibility and checks of your infrastructure’s health; it lets users add assertions via pre or post conditions to a Terraform configuration and/or modules, and then Terraform continuously checks to see if configurations or modules with assertions are passing. Terraform notifies users if it fails, minimizing risk, downtime, and costs.
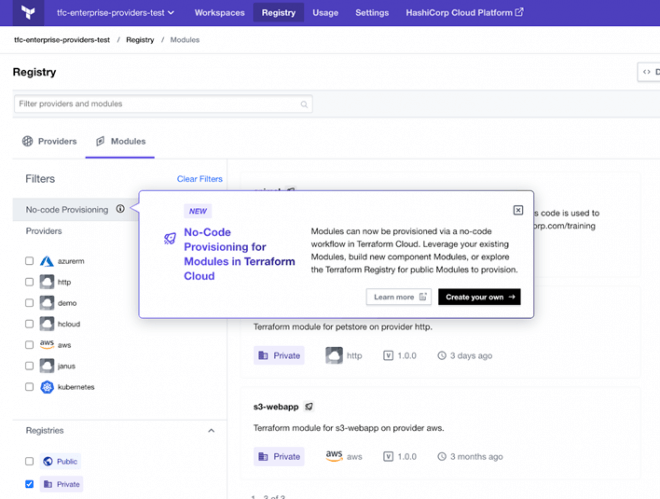
No-Code Provisioning Addresses the Skills Gap
The 2022 HashiCorp State of Cloud Strategy Survey found that skills shortages were ranked as the top multi-cloud barrier for technology practitioners and decision makers. Traditionally, provisioning something immediately useful with Terraform requires knowledge of infrastructure or networking as well as familiarity with HashiCorp Configuration Language (HCL), which can create a barrier to adoption.
The introduction of the private registry for Terraform Cloud and Terraform Enterprise made it easy to publish validated and approved modules that can be reused throughout the organization. But this degree of self-service only goes so far, as developers still have to select a module based on its contents, add it to a version control repo, create a workspace in Terraform Cloud, and provision the module from that workspace.
Given all of this, we wanted to offer greater self-service capabilities with a new no-code provisioning workflow. In addition, letting users avoid these various processes could reduce the number of people you need to train in Terraform.
With no-code provisioning, administrators and module publishers can manage a catalog of no-code-ready modules for users like application developers to deploy directly to workspaces. Developers can self-serve infrastructure from the Terraform private registry by selecting the no-code-ready module they need, entering the required variables, and deploying directly into a new workspace – all without writing HCL. Platform teams can now spend less time servicing repetitive internal requests and spend more time building on existing work to drive innovation and support the business.
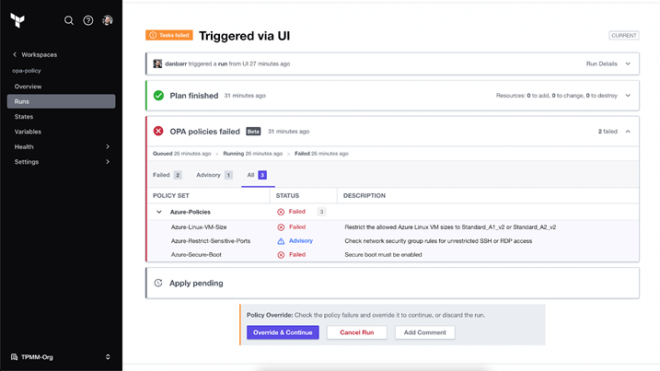
Managed Open Policy Agent for Terraform Cloud
As organizations grow in size and infrastructure complexity, they face increased risks of security breaches and non-compliance with regulatory requirements. To address this, in 2018, HashiCorp released Sentinel, a policy as code framework, and in August of this year, HashiCorp added Sentinel policies to the Terraform Registry so that experts can create and share reusable policies with the rest of their organization. We also announced the general availability of Run Tasks, which gives users the ability to extend Terraform policy enforcement using external services.
Today, we’ve introduced managed Open Policy Agent (OPA) for Terraform Cloud, which extends the policy as code features of Terraform Cloud to support OPA, based on the Rego policy language. Support for OPA in Terraform allows customers who have already standardized on OPA to bring those policies along with them into Terraform Cloud. OPA works alongside Sentinel to increase the number of supported ways for customers to adopt a policy as code framework for secure multi-cloud provisioning.
More Terraform Updates
Outside of the keynote announcements, we’ve made several additional enhancements to the Terraform workflow:
Azure Provider Automation
Today we announced the availability of the Azure Provider Automation tool, which ensures that users are able to utilize the new resources and services of the Azure Resource Manager in Terraform Azure provider quickly. This feature automatically generates newly added or modified Azure resources so Terraform users can benefit from new or updated features when they are released by Microsoft.
ServiceNow Service Graph Connector for Terraform
We’ve also introduced ServiceGraph Connector for Terraform, a cloud-based single system of record for IT infrastructure and digital service data. This integration gives ServiceNow customers information about Terraform infrastructure state and resources that were generated from ServiceNow. Users can now leverage this integration for full visibility on cloud resource tracking, with the ability to see which resources have been provisioned and see who created them.
Terraform Plugin Framework (Beta)
Terraform Plugin Framework has reached beta phase with a redesigned provider development experience that exposes all available Terraform functionality to providers and enables more readable code. Developers can get started to build the providers using our new HashiCorp Learn guide or upgrade their existing provider using our migration guide. Learn more about Terraform Plugin Framework here.
Learn More and Try Terraform Cloud
Continuous validation, no-code provisioning, and managed OPA with Terraform Cloud are available today as public beta features. To learn more about no-code provisioning, attend the Set up a No-Code Provisioning Workflow with Terraform Cloud webinar on Tuesday, Nov. 1. If you are not yet using Terraform Cloud, you can sign up for free.
Lees ook:
- HashiCorp breidt Zero Trust security oplossing uit met secure remote access in de cloud
